I have to give HTB some credit for their labs. I always walk into them thinking that I totally know how to finish them. 3-4 hours later, I have learned some new subject/tools and have had to read up on a few other walkthroughs to finish them.
This one was unfortunately no different in that case.
I learned a lot though about RSA and OpenSSL, the difference between symmetric and asymmetric encryption, and a new tool called RsaCtfTool.
As always here is the link to my original notes if you want to take a look at the different paths I explored. I also streamed some of this lab.
Let’s get started.
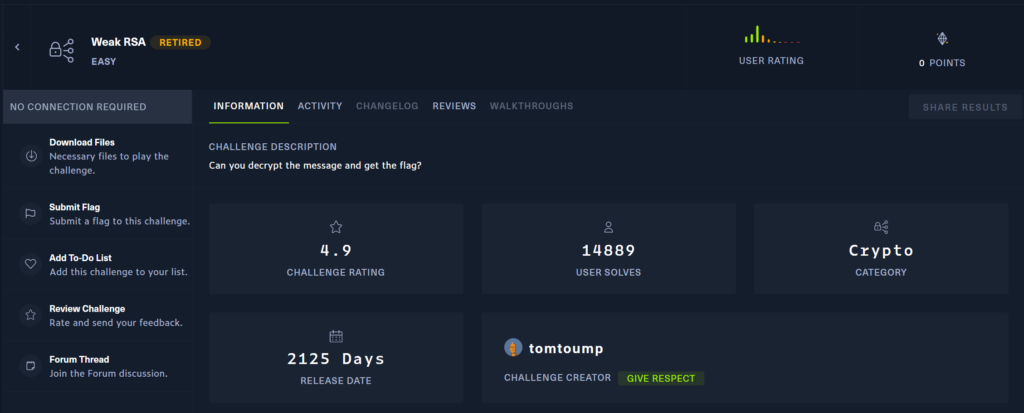
When opening up the lab, you’ll be given a downloadable zip file that can be extracted on your computer with the following password:
zip password --> hacktheboxWhen you have downloaded the zip file, you can confirm it’s the correct file with the following SHA256 HASH:
1cbf890e7a0fe8b404597b565da96c388e5653937631e2dc8710ede9d15bdb7d After extracting the contents of the zip file you’ll be given two files. An encrypted flag file called flag.enc and a public key file named key.pub.
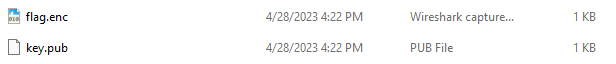
Checking out what is in the key.pub file, we find it to be a “short” public key. Note, I am using Kali to analyze and work with the files.
cat [Path to key.pub]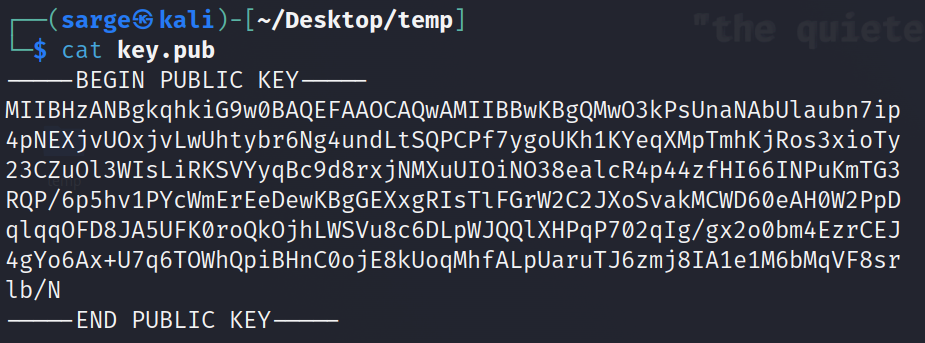
-----BEGIN PUBLIC KEY-----
MIIBHzANBgkqhkiG9w0BAQEFAAOCAQwAMIIBBwKBgQMwO3kPsUnaNAbUlaubn7ip
4pNEXjvUOxjvLwUhtybr6Ng4undLtSQPCPf7ygoUKh1KYeqXMpTmhKjRos3xioTy
23CZuOl3WIsLiRKSVYyqBc9d8rxjNMXuUIOiNO38ealcR4p44zfHI66INPuKmTG3
RQP/6p5hv1PYcWmErEeDewKBgGEXxgRIsTlFGrW2C2JXoSvakMCWD60eAH0W2PpD
qlqqOFD8JA5UFK0roQkOjhLWSVu8c6DLpWJQQlXHPqP702qIg/gx2o0bm4EzrCEJ
4gYo6Ax+U7q6TOWhQpiBHnC0ojE8kUoqMhfALpUaruTJ6zmj8IA1e1M6bMqVF8sr
lb/N
-----END PUBLIC KEY-----
Next, I’ll check out the flag.enc file.
cat flag.enc
Makes sense that the file would be a bunch of gobblygoop as it is encrypted. I won’t walk you down all of the hopeless paths I took but will outline some of them just for reference:
- Looked at the binary with a hex editor.
- Thought I could do something with magic numbers.
- Spent way too much time with John The Ripper thinking I could do something with it.
Finally, I gave up and looked through another person’s walkthrough. Actually, I looked through quite a few walkthroughs because I wanted to see if someone had solved the lab with John. Unfortunately, the three I went through all used the same tool. I really wanted John to be the answer for some reason.
It appeared that everyone else’s walkthroughs used a tool called RsaCtfTool to create a private key.
It’s a pretty handy tool and I will keep it accessible for future use. Check out the Github page for it above and they’ll have instructions for downloading the tool and using it for other purposes.
I won’t try to bother explaining how the tool works here as it is so far past my level of comprehension on crypto that I would sound like an idiot. I keep seeing common words though like factorization.
A new goal of mine –> Learn what factorization means.
Besides that, once the tool is downloaded, it is capable of breaking “Weak” public keys to create the private key. This is an important note though as it is able to do this with “Weak” keys. For those familiar with RSA keys, the one given to us is really small.
So let’s begin:
./RsaCtfTool.py --publickey [Path to public key] --privateThis will generate a private key for us which we can save to its own file called key.priv.
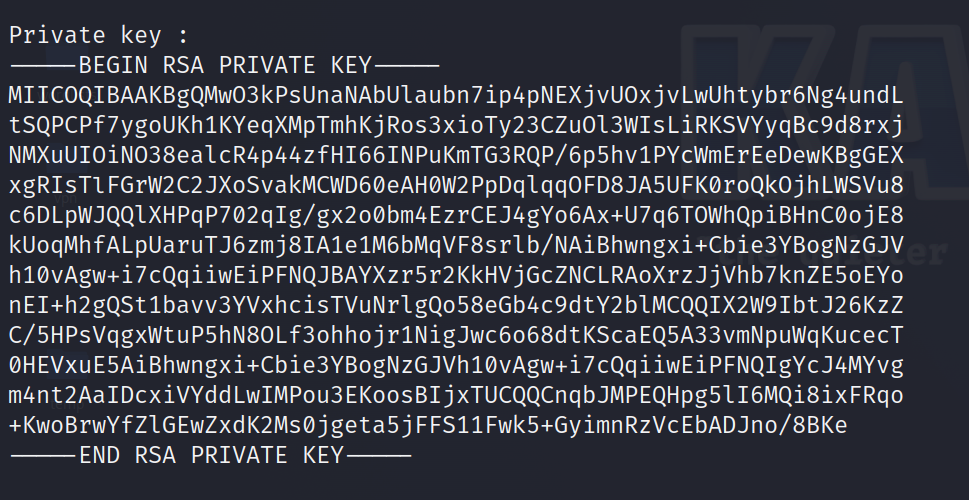
The next command we will use is the Openssl command to decrypt the flag.enc file with the newly generated private key.
openssl pkeyutl -decrypt -in [Path to encrypted file] -out myfile_decrypted.txt -inkey [Path to key.priv]This will generate a decrypted file called myfile_decrypted.txt.
You should now be able to view the decrypted text file and get the answer.
Conclusion
Once you know what to do, it is a pretty easy lab. I however was too focused on using the tools I did know how to use instead of searching for new tools. A quick Google search at the beginning could have told me about RsaCtfTools and helped solve this problem much more quickly.
Lesson learned.
As always, thanks for reading and catch you all later.
-sgtdiddlywink