Hashes are, to say the least, really cool. While I only understand a fraction of how the algorithms work and how cryptographers and mathematicians come up with them, I still think they’re really cool.
For those not familiar with what a hash is, or more correctly what a hash function is, I’ll give you the technical definition first and then a simpler definition that I understand.
Technical definition: A hash function is a mathematical function that takes an input (often referred to as the “message” or “data”) of any length and produces a fixed-size output, typically a string of characters or bytes. The output value is often called the “hash value”, “message digest”, or “checksum”.
ELI5 definition: If you have a hunk of beef and put it through a grinder, you end up with hamburger. The hunk of beef is your data/message, the grinder is your hash function, and the hamburger is your hash. In the case of a hash function, it turns the data into a jumbled string of characters that is infeasible to reverse. Much like the hamburger.
Now you might be wondering, how is this useful? That is a really good question. There are a ton of uses for hash functions, but the one we will concentrate on pertains mostly to credentials, or more specifically, passwords.
Let’s take a step back and picture a scenario. Before hashing passwords became a regular process in most modern web applications, you would go to your favorite website, let’s say Facebook, and plug in your email address and password. These would be passed to the database that holds all of the usernames and passwords. The two would be queried to determine if the username and password match, and if so, you were given access to your page.
And that was great until it wasn’t. Essentially what web applications then had was a giant database of all of the usernames and passwords. If a hacker were to break into the database, they then have access to everyone’s password and can log into their accounts immediately. This is a really bad thing if you haven’t guessed.
This is where the magic of hashing comes in. When Facebook decides to hash all of their passwords, they end up deleting all of the “clear text” passwords and instead associate a unique hash with your username. When you go to log in, you’ll still plug in your username and password, but this time, the app will hash your entered password (using the same hashing function) and compare it to the database. If the hashed password matches up with the hashed password in the database, then you get access.
If this concept is too new to you, you may be wondering, as I did, how this helps. Well, when an individual now breaks into an app’s database, all they have is a table of usernames and hashed passwords. They can’t input the hashes into a login window, they can’t “easily” crack the hashes, and now the company that owns the compromised app has time to alert its users to change their passwords.
That is the basic gist of the entire idea. Of course, there is far more complexity to it if you want to dive into the weeds, such as salting, rehashing, etc., but this gives an important layer of security to your credentials.
As I mentioned before you can’t easily crack hashes. However, hash functions regularly utilized 10 years ago are no longer valid because computing power has given us the ability to crack those hashes relatively easily. In some cases, hashes can be reversed, but the workaround that hackers came up with is to create giant dictionaries or rainbow tables. The basic idea is that if you were able to obtain a hash and you knew the hashing function used for it, you can take that and compare it to a table of characters that have already been hashed.
Oh, and these aren’t small tables either. We’re talking, in some cases, millions of hashes.
Now, this isn’t to say that it’s as easy as Googling the cracked hash, but in some instances, it definitely is. That is why so many apps require a certain number of characters and character types. The goal is to create a value that will take a vast amount of resources and time to eventually crack the hash.
I could spend more time going into this, but keep Googling if you want more information, as there are plenty of resources available on the subject.
I want to dive into this lab and start cracking hashes. My goal for this lab was to take as much time as needed and avoid using hints. I wanted to challenge myself to see how much I could figure out on my own, and for the most part, I’m pretty happy with the outcome.
As always, feel free to read through my Gitbook for my original notes on the matter.
LEVEL 1
HASH –> 48bb6e862e54f2a795ffc4e541caed4d
I’m working on trying to get a basic understanding of how hashes look to easily identify them if I need to so I usually start with counting the characters and determining what character set they are using.
In this case, it is 32 characters with the characters being hexadecimal (0 – f). Just looking at this my first thought was MD5 which tends to be an older hash function.
Now, I’m pretty sure the lab wanted me to use the internet’s resources on Level 1 to crack these hashes but I already had a pretty good understanding of how hashcat worked so I went there first. If you are not familiar with the tool, I’d highly recommend checking it out and getting a good understanding for it.
To run hashcat use the following:
hashcat -m 0 [HASH] [PATH TO WORDLIST]-m specifies the hashing function to be used which can be found by either going to the help menu or checking out their website.
0 – indicates an MD5 hash function
HASH – The has can either be a file with a list of hashes for convenience or directly typed in.
WORDLIST – I used the rockyou.txt password list which can be found on most Debian OS under /usr/share/wordlists/rockyou.txt.gz or at this GitHub link.
Once the tool has run, it should state whether it found a match. If it did you can use the following to see the original hash and the cracked hash:
hashcat -m 0 [HASH] [PATH TO WORDLIST] --showHASH –> CBFDAC6008F9CAB4083784CBD1874F76618D2A97
A quick lookover shows that this hash is 40 characters long consisting of hexadecimal characters. I did a quick Google search and found that this is most likely SHA1 function. However, we also have another way to check what function to use. Hashcat can sometimes recognize hashes and provide you with some possible options.
hashcat [HASH]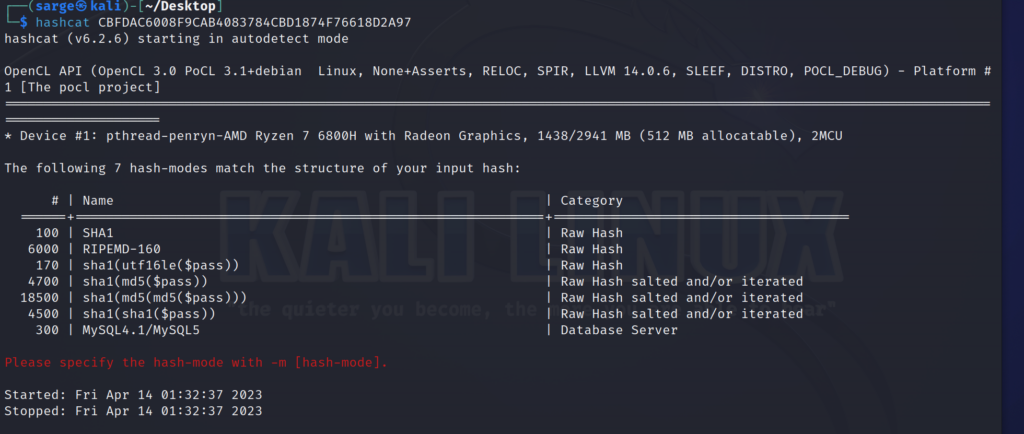
In this case, I’ll go with SHA1 which has the flag -m set to 100.
hashcat -m 100 [HASH] [PATH TO WORDLIST]If hashcat discovers an answer it will let you know and all you have to do is kick out the –show option.
hashcat -m 100 [HASH] [PATH TO WORDLIST] --showHASH –> 1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032
Running the hash initially through hashcat shows us that it is most likely a SHA2-256 function with the -m flag set to 1400.
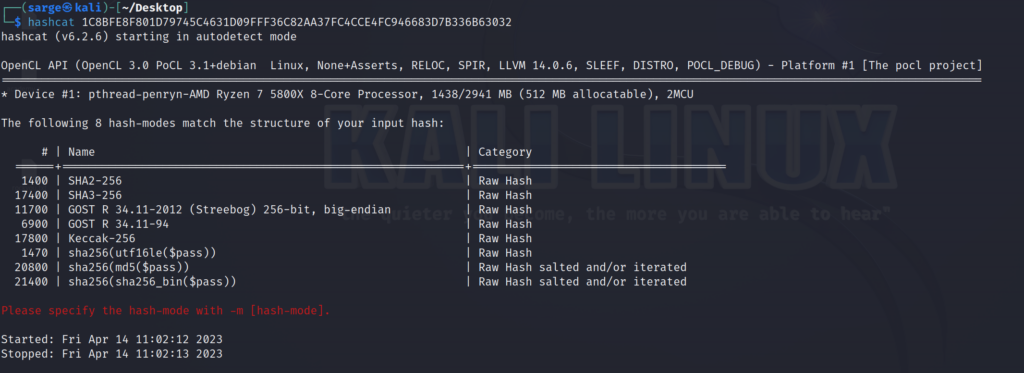
hashcat -m 1400 [HASH] [PATH TO WORDLIST]As before, if it was right, it should kick out an answer with the following:
hashcat -m 1400 [HASH] [PATH TO WORDLIST] --showHASH –> $2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRom
This one is a bit different than the others in the fact that it is utilizing Bas64 Encoding and is 60 characters long.
Running it through hashcat doesn’t give us a clue so we’ll have to google around for it.
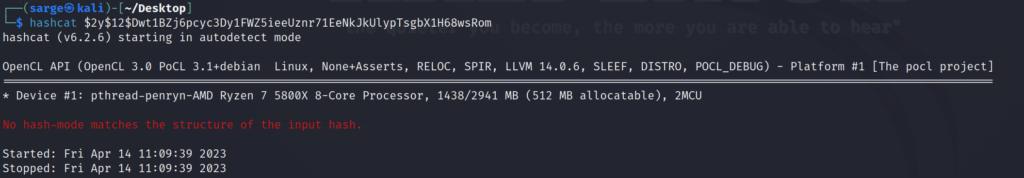
After a bit of Googling, I found that the most likely function used to create this hash is bcrypt. Bcrypt is a very resource-intensive hashing algorithm so brute-forcing the password may not be the best bet unless we want to wait around for a few days.
Since I know it is most likely using a bcrypt function, let’s search through hashcat’s function table for possible options.
hashcat --help | grep bcrypt
Looks like we have a few options so let’s start with the first one that has the flag -m set to 3200.
To save time, the answer box only shows four characters so we know the cracked hash has to be four characters. This should help out drastically when running through our rockyou password list which is somewhere in the range of 1.5 million passwords. Run the following to filter out all passwords in the list that are exactly four characters and create a new file.
grep -E '^.{4}$' [PATH TO WORDLIST] > rockyou_4.txtAfter you have created the new password list, run it through hashcat.
hashcat -m 3200 [HASH] rockyou_4.txtThen run the –show option to see the results.
hashcat -m 3200 [HASH] rockyou_4.txt --showHASH –> 279412f945939ba78ce0758d3fd83daa
This one appears to be 32 characters hexadecimal. Running it through hashcat shows us that it is most likely MD4 with the -m flag set to 900.
This may be a bit more difficult as based on the answer box, the cracked hash is going to be 10 characters long. Most likely the 10-character limit is going to surpass most wordlists that are available to us and take a significant period of time to crack.
So let’s go online and see what we can’t find. Doing a quick Google search gives us a website called Hashes.com which gives us a neat tool to run hashes through rainbow tables that have already been created.
Running this hash through their hash search not only confirms that it is MD4 but will also give us the answer.
LEVEL 2
HASH –> F09EDCB1FCEFC6DFB23DC3505A882655FF77375ED8AA2D1C13F640FCCC2D0C85
Similar to before, let’s run the hash through hashcat to see what function was possibly used to create it.
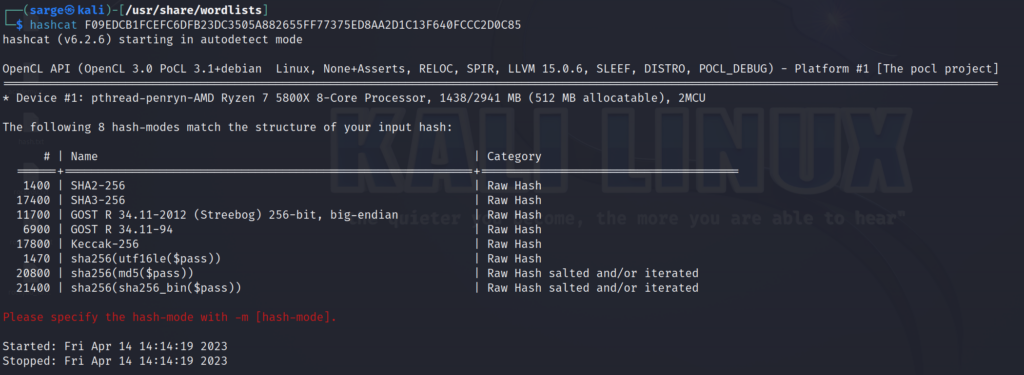
Going with the top function we will set the -m flag to 1400.
hashcat -m 1400 [HASH] [PATH TO WORDLIST]If this works then use the –show command to display to original hash and the cracked hash.
hashcat -m 1400 [HASH] [PATH TO WORDLIST] --showHASH –> 1DFECA0C002AE40B8619ECF94819CC1B
This initially looks to be another MD4 hash. However, if you run through the similar steps above you’ll notice you don’t get any answers outputted from hashcat. Checking with hashcat to see what possible functions are used, shows us we have a few options.
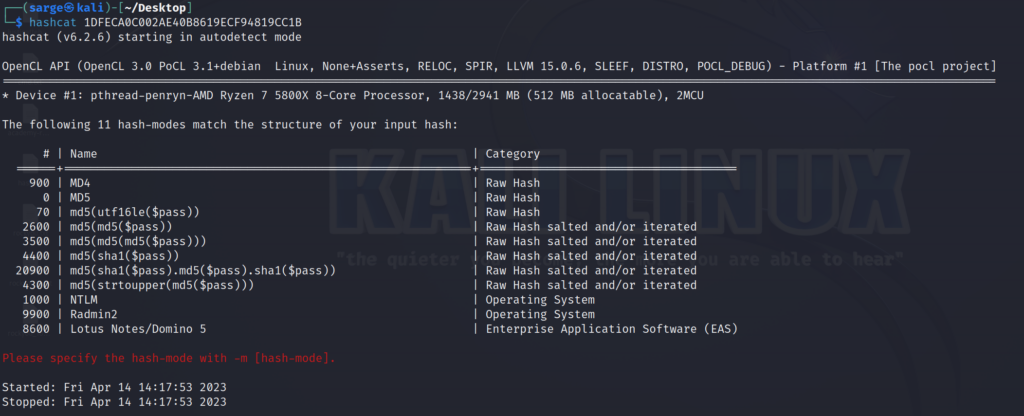
Let’s run the hash through hashes.com website above to see if it can tell us anything.
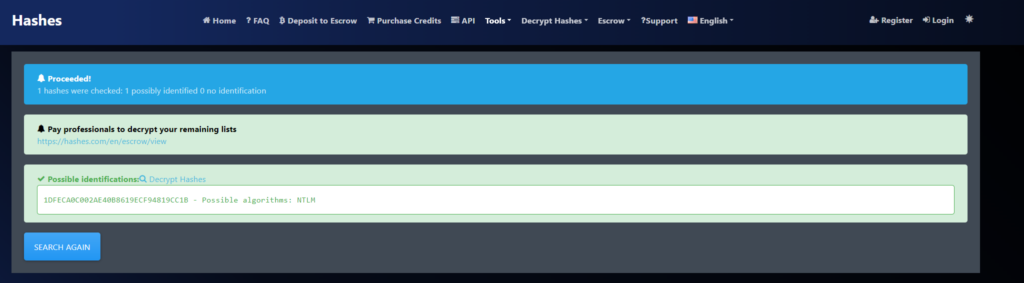
Based on this information, let’s set the -m flag to 1000 for NTLM and run it through hashcat.
hashcat -m 1000 [HASH] [PATH TO WORD LIST]If successful, we should be able to view the cracked hash with the –show option.
hashcat -m 1000 [HASH] [PATH TO WORD LIST] --showHASH –> $6$aReallyHardSalt$6WKUTqzq.UQQmrm0p/T7MPpMbGNnzXPMAXi4bJMl9be.cfi3/qxIf.hsGpS41BqMhSrHVXgMpdjS6xeKZAs02.
This one is interesting as it gives a salt with the hash. For those of you who are not familiar with salting, I’ll try to quickly cover it here.
Salting passwords is the process of adding a random string of characters to “usually” the end of the given password from the user. This is automatically done prior to hashing. The salt is then usually stored with the hashed password in a database.
This in turn helps to create an even more complex password and results in making a more difficult hash to crack.
As stated in the question, the salt is:
SALT –> aReallyHardSalt
We can also see this appended to the front of the hash itself.
Running this initially through hashcat will not give us any results on the possible function so let’s run it through hashes.com.
When we run it through the website, it looks like the function being used SHA512 but they also have the cracked hash with it.
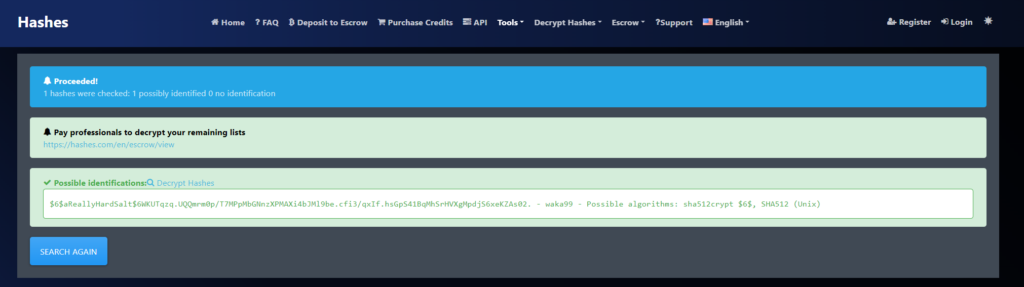
HASH –> e5d8870e5bdd26602cab8dbe07a942c8669e56d6
SALT –> tryhackme
Similar to the previous hashes, let’s run it through hashcat to get an idea of the function being used.
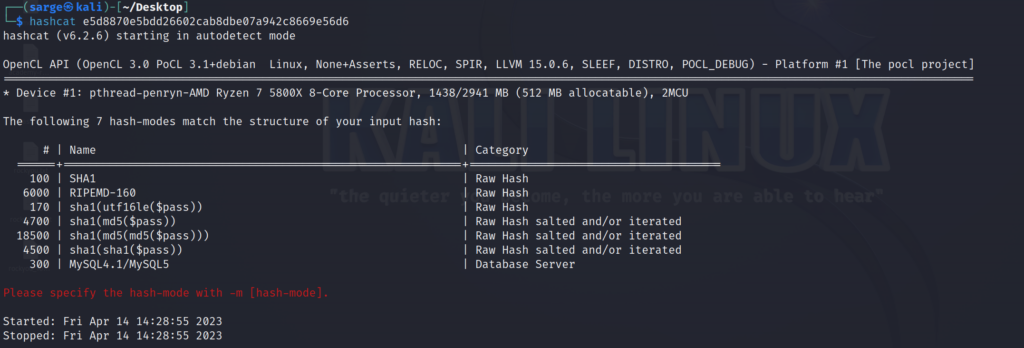
It appears that it is most likely SHA1 but we’ll have to use a different -m flag to other than 100 to take into account the salt.
None of these fit the bill for the right function so let’s go search the rest of hashcat’s table to see if we have other SHA1 functions not being displayed.
hashcat --help | grep SHA1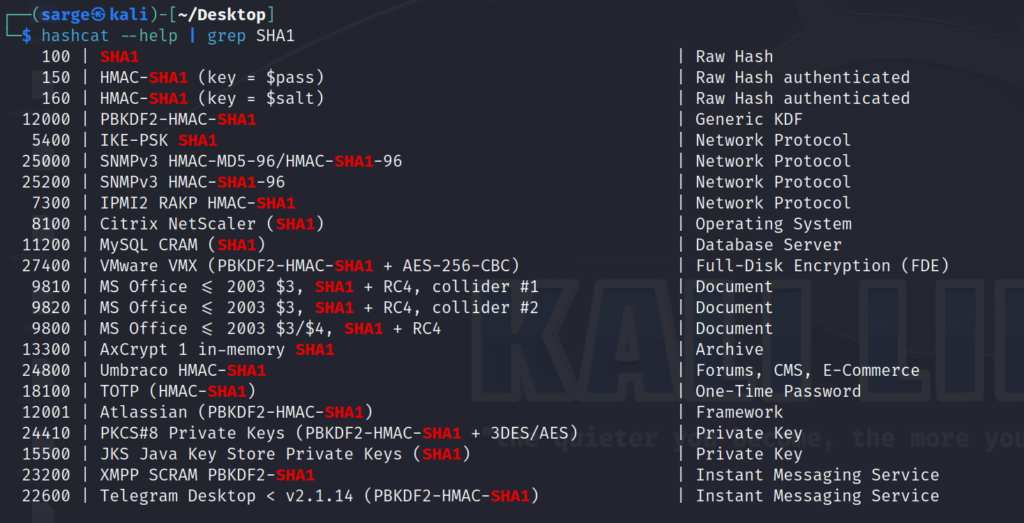
It looks like we should be interested in HMAC-SHA1 (key = $salt) with an -m flag set to 160. There will also be one other change we need to make to the given hash. We need to combine the hash and the salt with a colon.
hashcat -m 160 -a 0 [HASH]:[SALT] [PATH TO WORDLIST]Afterward, run the –show option to see the results.
hashcat -m 160 -a 0 [HASH]:[SALT] [PATH TO WORDLIST] --showCONCLUSION
This was a great lab for learning about different hashes, different tools to crack them, and to get practice with recognizing them. I hope you were able to get through this lab and maybe get some support from this walkthrough.
As always, thanks for reading and catch you all later.
-sgtdiddlywink